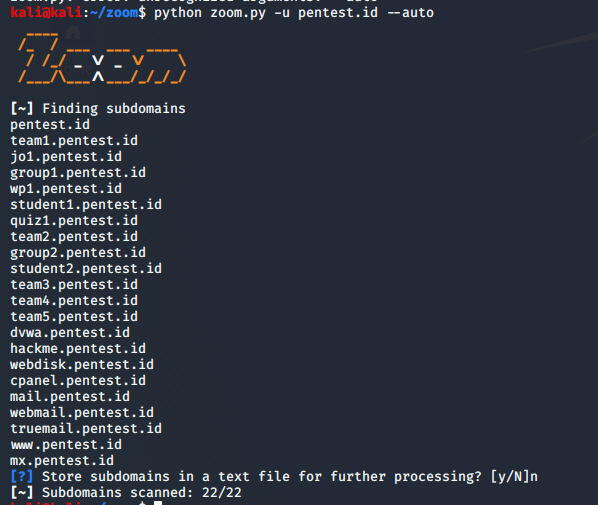
In this session, we learned about Source of Network-Based Evidence and Principles of Internetworking.
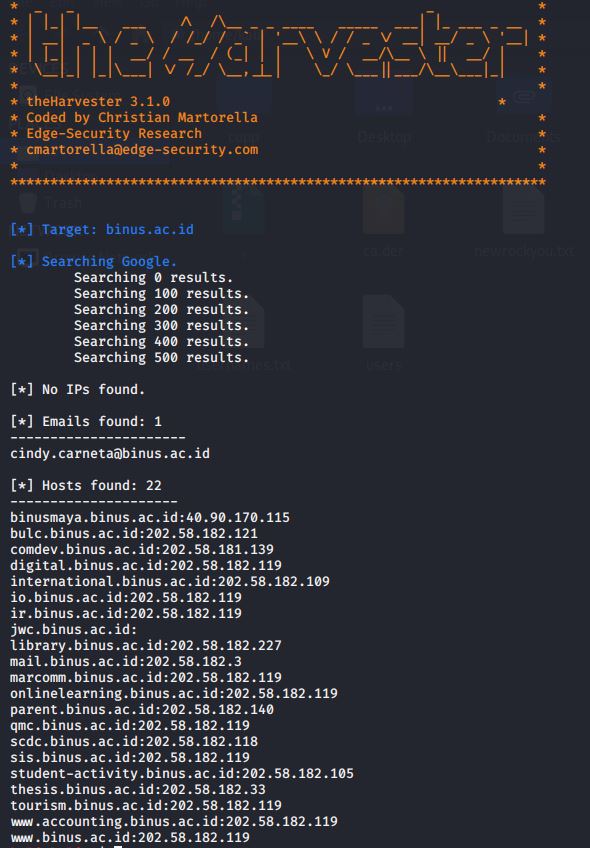
There are many different types of network-based evidence which are:
- On the wire
- In the air
- Switches
- Routers
- DHCP Server
- DNS Server
- Authentication Server
- NIDS/NIPS
- Firewalls
- Web Proxies
- Application Server
- Centralized Log Server
- Modem
On the wire refers to physical cabling that carries data over the network. There are 3 different tap types which are vampire tap, surreptitious fibre tap, and infrastructure tap.
In the air works as a wireless station to station signals where it checks radio frequency and infrared to obtain management and control frames, access point names, MAC addresses and traffic analysis.
Switches are physical connection between network segments where it can be used to capture and preserve network, and to mirror traffic from one port to another.