This tutorial is 100% for Education Purpose only. Any time the word “Hacking” that is used on this site shall be regarded as Ethical Hacking. Do not attempt to violate the law with anything contained here. If you planned to use the content for illegal purposes, then please leave this site immediately! We will not be responsible for any illegal actions.
Another method of creating a password list that is to be used for brute force is by using CeWL. This tool will take the words used in a site and append them into a list.
To start, type:
$ cewl -w passwords.txt -d1 -m5 target_url
–w passwords.txt will create the passwords.txt file that will consists of the list of words obtained from the site
–d1 defines the depth in which CeWL will crawl the website. 1 indicates that it will stay on this exact site and not open any links on it.
–m5 defines the minimum length of the word that will be put in the list. In this case the minimum length is 5.
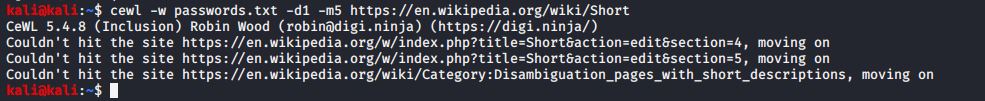
Below is the passwords.txt generated